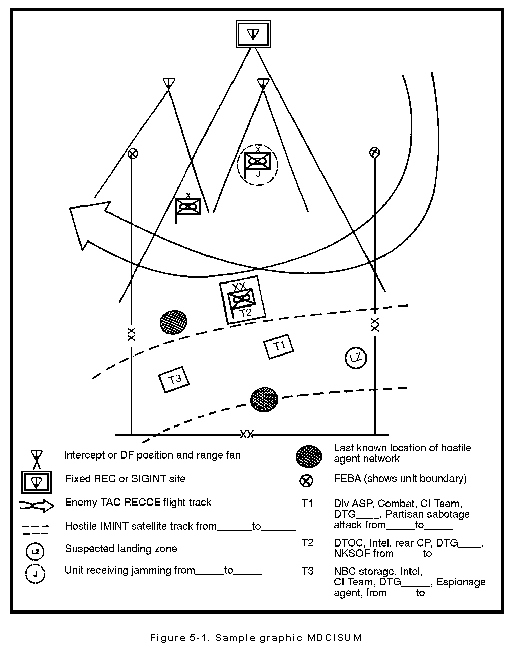
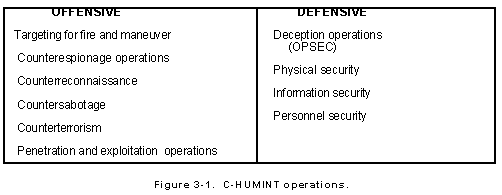
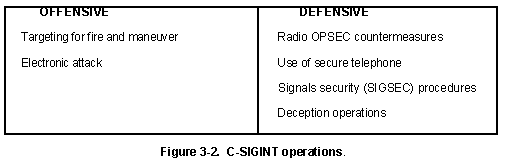
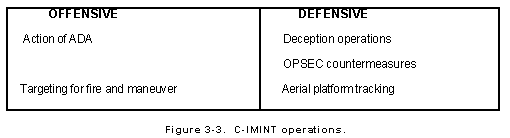
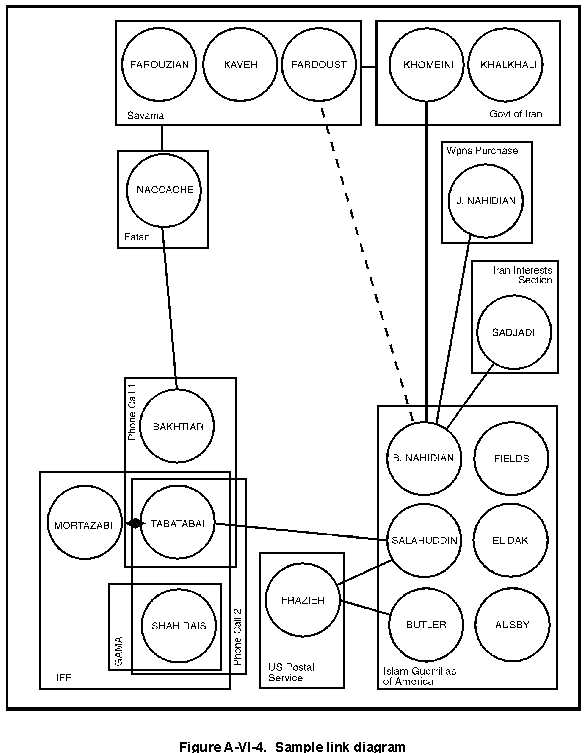
Four-sector counterintelligence matrix (adapted from Duvenage & von... | Download Scientific Diagram
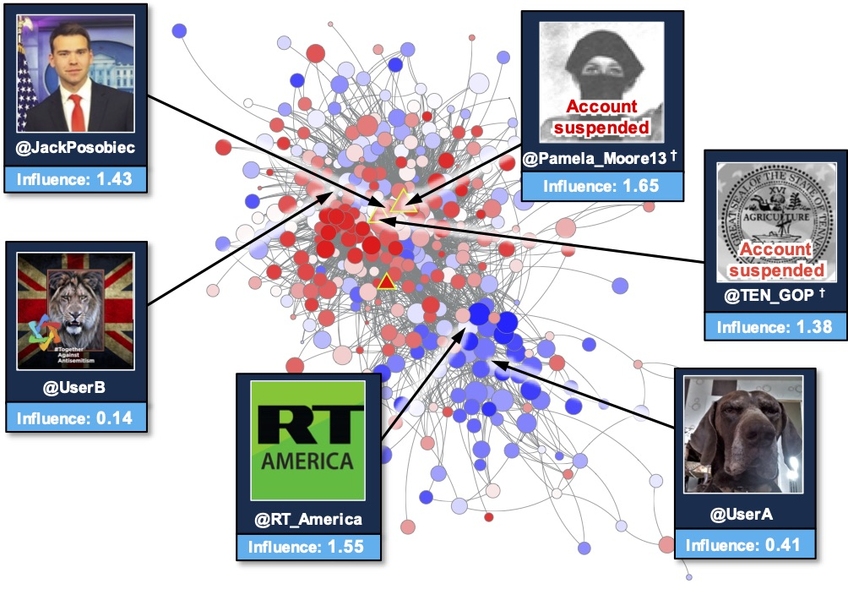
Artificial intelligence system could help counter the spread of disinformation | MIT News | Massachusetts Institute of Technology

COMPETITIVE INTELLIGENCE AND COUNTERINTELLIGENCE – MODERN TOOLS FOR GENERATING PROACTIVE CORPORATE SECURITY | Semantic Scholar